How Long Should You Retain HIPAA Audit Logs?
“Do I really need to retain all my HIPAA audit logs for 6 years?”
We hear this question a lot from organizations, and as you may already understand, the answer isn’t straightforward. Some might tell you that yes, all audit logs in your ePHI environment need to be retained for at least 6 years, but things are a bit more complicated than that—especially for business associates.
As practiced HIPAA assessors who understand how complicated and high stakes this type of compliance is, we want to provide some insight. In this article, we’ll break down the actual specific HIPAA requirements in the law that reference logs, other frameworks with helpful information, and finally, our recommended course(s) of action.
Let us decrypt a complex topic so that you get the clarity you need to ensure you stay in compliance with HIPAA.
HIPAA Log Requirements
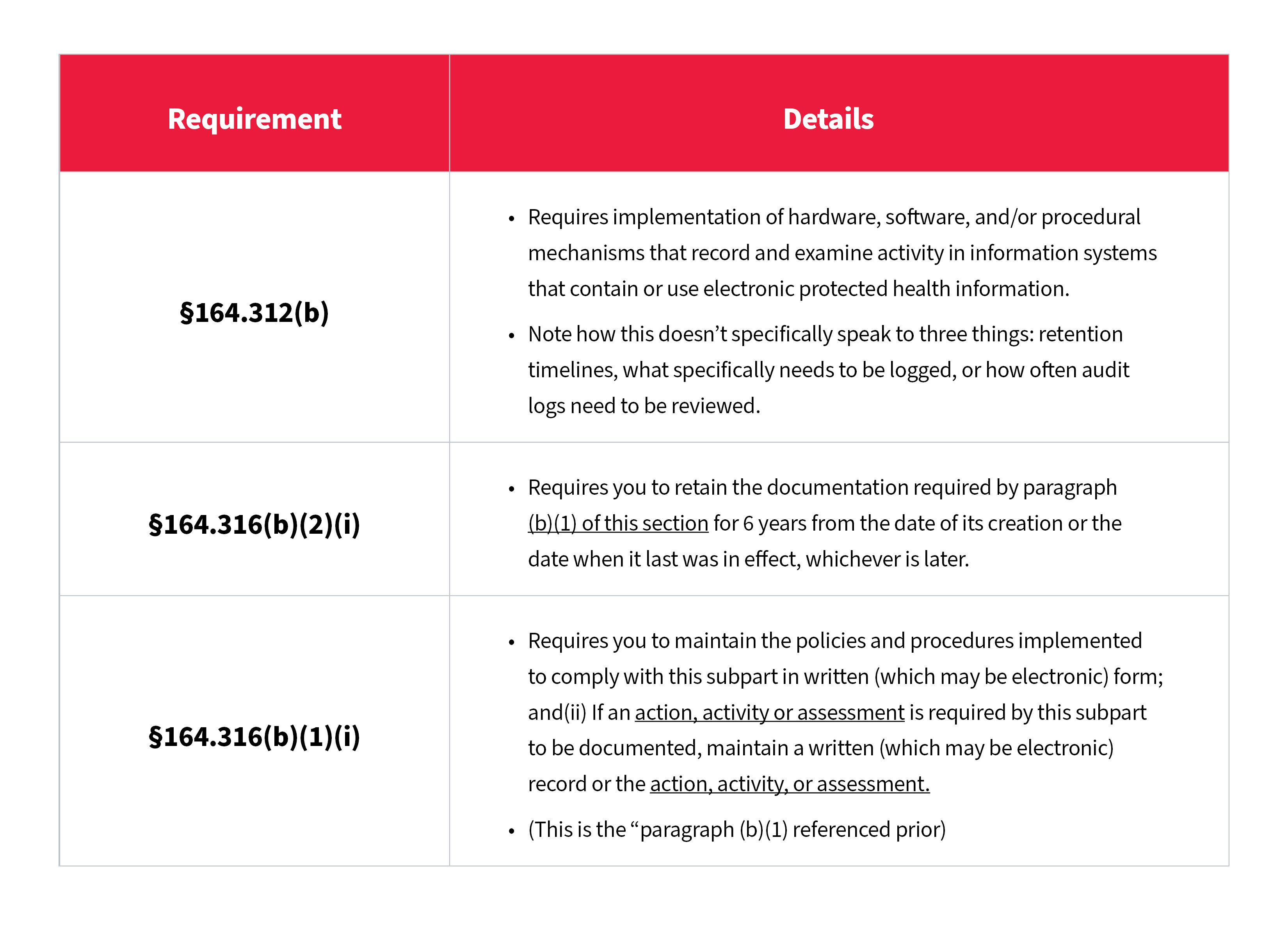
When you try to find the crux of these and how they fit together, you must ask whether all actions/activities logged in an ePHI environment that end up in audit logs are considered an “action, activity, or assessment” as defined by HIPAA?
- If they are, then you have a clear-cut case of the 6-year requirement applying to audit logs for systems in your ePHI environment.
- But if they aren’t, or maybe only certain types of audit actions/activities are, things get complicated.
That’s because the HHS has not actually defined if all details captured in audit logs are considered an “action, activity, or assessment,” nor has it defined what technically falls under these categories. For instance, operational logs don’t have stated retention requirements, but then HIPAA hasn’t defined what operational logs are either.
Additional Information Regarding HIPAA Logs
More than that though, other documents that reference HIPAA log retention might better inform your understanding.
- HHS “Understanding the Importance of Audit Controls” Newsletter
- To their credit, the HHS did put out this bulletin in January 2017 that stated, “audit trails’ main purpose is to maintain a record of system activity by application processes and by user activity within systems and applications.”
- “Activity” is one of those three magic words referenced in the aforementioned §164.316(b)(1), so you could interpret this to mean items in audit logs fit the definition of “activity;” therefore, the audit logs that include the details of these activities need to be retained at least 6 years.
However:
- This publication didn’t mention 6-year audit log retention specifically (it didn’t mention any required retention, for that matter). It also reiterated that the HIPAA Security Rule does not identify what information should be collected from an audit log nor even how often those logs should be reviewed—rather, your risk analysis and other organizational factors should determine that.
- The HIPAA Security Rule was not architected in a prescriptive way by design, and so it seems reasonable then that the decision of how long to retain audit files falls to you, assuming you factor in your risk analysis. Still, the level of risk that some Business Associates might have regarding logs can be very different than that of a Covered Entity.
- NIST SP 800-92 (Guide to Computer Security Log Management) also refers to HIPAA audit log retention:
- It also mentions NIST SP 800-66 (An Introductory Resource Guide for Implementing the HIPAA Security Rule)—Section 4.22 says “documentation of actions and activities need to be retained for at least six years.”
- In this context, it appears NIST’s interpretation of “actions and activities” in HIPAA would include all audit logs. And while NIST doesn’t determine HIPAA compliance, the Office of Civil Rights (OCR) refers to NIST in HIPAA guidance as solid advice.
- So, you could take all that to mean if NIST SP 800-92 confirms audit logs in this category of action and activities when referring to NIST SP 800-66, they need to be retained for at least 6 years per the HIPAA requirement.
Should You Retain All HIPAA Audit Logs for 6 Years?
That’s all the documented considerations, but the question remains: how long do you keep your logs?
As an assessor, here’s our perspective. Save all audit logs for at least 6 years if:
- It’s not cost-prohibitive to your organization; and
- The logs contain information that is related to actions on systems containing ePHI.
That’s the safest move, but that may not work for many organizations, so here are the concession we’d offer to them, keeping in mind that HIPAA doesn’t specify what you need to log, how often you need to review logs, or what constitutes an “action, activity, or assessment” in the aforementioned requirement §164.316(b)(1)(i):
- HIPAA is built in such a non-prescriptive way—as we mentioned before, organizations are meant to rely heavily on their individual risk analysis/risk management programs, so it would make sense that your log retention timeline too would require consideration of risk or specific impact to your organization—rather than the strict 6 years.
- It seems to us then that organizations do have freedom in terms of what you determine to be the critical actions/activities you need to log and retain for at least 6 years:
- If you categorized higher risk activities to be documented in audit logs to be retained for the 6 years, you could then judge retention for the operations-type logs based on your risk analysis—while these could be relevant to your ePHI environment, they may not meet that level of risk to require 6-year retention as clearly as those of higher risk.
Questions may still arise, but if you can clearly demonstrate you considered audit log retention as part of your risk analysis/risk management program based on the type of activities being logged, you should have a solid and supported explanation in terms of why you didn’t also retain your other audit logs for 6 years.
Next Steps for Your HIPAA Compliance
While it may be frustrating that the governing bodies haven’t been more specific around this subject, hopefully, these details and the inclusion of other resources have provided at least some clarity. Of course, you may still feel a bit hesitant, and it’s no wonder—HIPAA penalties are no small thing.
But remember that, historically, the OCR has been clear it’s your risk analysis and risk management program that should drive your HIPAA control selections. So, if you take a risk-based approach, you can find the audit log retention plan that best fits the nature of your organization and your services provided in the healthcare provider chain. You’ll also be in the best position to support your chosen approach should the OCR seek an explanation.
If you’re still seeking an explanation—on HIPAA audit logs or otherwise—we would encourage you to reach out to us so that we may put any further concerns to rest. In the meantime, be sure to check our other content, which can help you continue demystifying the details of compliance for those in healthcare:
About DOUG KANNEY
Doug Kanney is a Principal at Schellman based in Columbus, Ohio. Doug leads the HITRUST and HIPAA service lines and assists with methodology and service delivery across the SOC, PCI-DSS, and ISO service lines. Doug has more than 17 years of combined audit experience in public accounting. Doug has provided professional services for multiple Global 1000, Fortune 500, and regional companies during the course of his career.




